Tutorial 1: Intro to Threat Intelligence
As you step through this workshop, you’ll notice that each page with a video duplicates the lesson in both video and written form. You can follow one or the other depending on what type of learner you are.
What is Threat Intelligence?
Threat Intelligence Analysts:
Learn about adversaries … and share knowledge with public/private sector partners
Track adversaries over time … to understand the changing threat landscape
Implement defenses … and work with product development teams to protect customers
Data alone does not equal intelligence. Security logs on their own don’t tell you anything impactful until you process them. Once a threat intelligence analyst processes the data and information, with the context of the adversaries they track and the context of the changing of the threat landscape, they can begin coming up with a story and timeline of what my have happened. To understand what those threats mean, why they have occurred, and how it has affected your company … that is true threat intelligence.
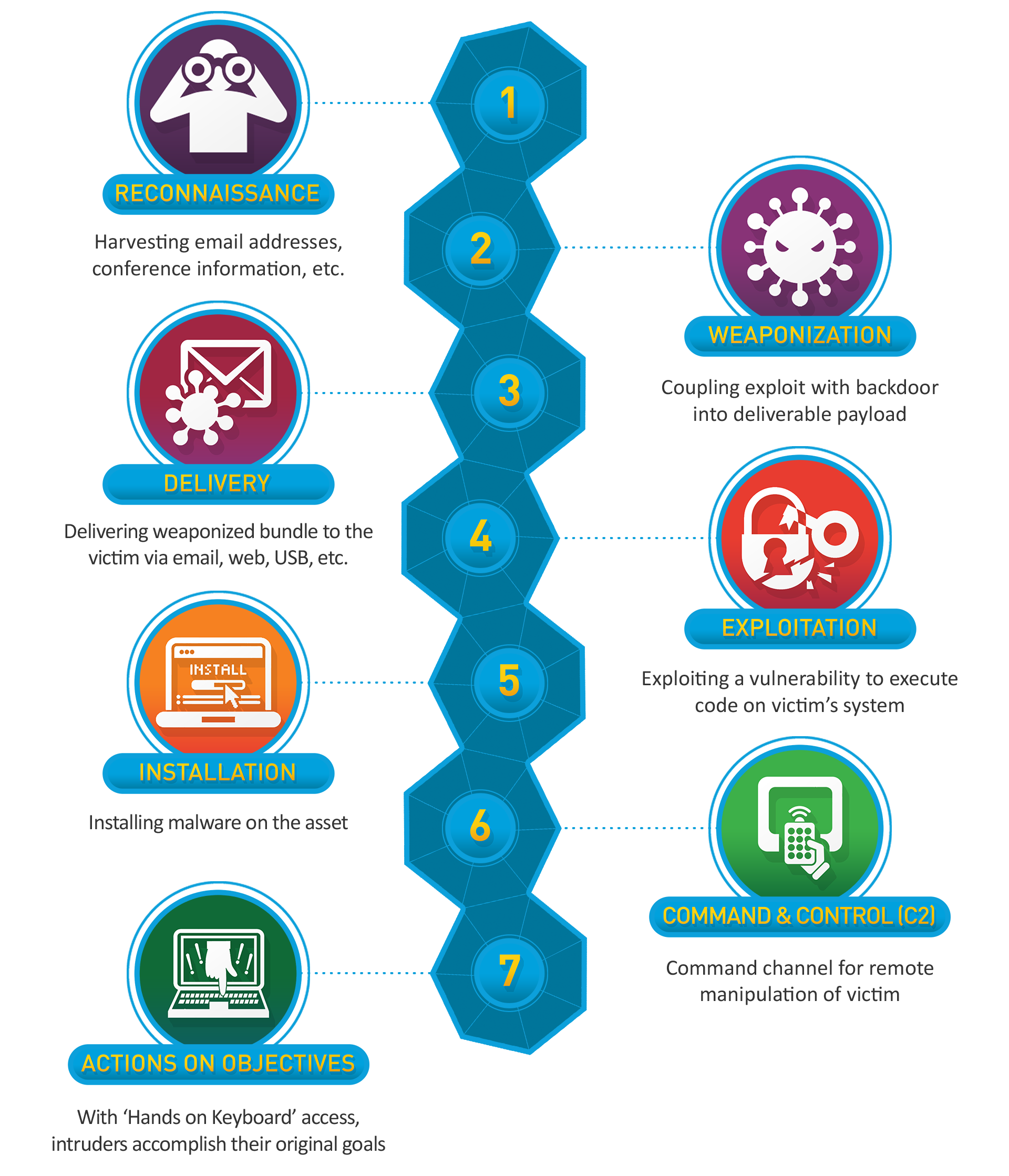
What is the Cyber Kill Chain?
The Cyber Kill Chain, originally developed by Lockheed Martin, is a framework for identifying and preventing cyber attacks. This framework identifies 7 steps that adversaries must complete in order to achieve their objective 1 .
Understanding the Diamond Model
The Diamond Model of Intrusion Analysis provides a method for analyzing the characteristics of cyber attacks. This model emphasizes the relationships between 4 components: the adversary, capabilities, infrastructure, and victims. The theory this is based on is that for every cyber attack, there exists “an adversary taking a step toward an intended goal by using a capability over infrastructure against a victim to produce a result” 2 .

What is KC7?
This leads us into why we chose to call this game KC7; because it helps step people through the 7 stages of the Cyber Kill Chain described above.
KC7 is a game designed to teach people how to apply cybersecurity knowledge and develop analysis skills using realistic data. It is a unique and immersive cybersecurity analysis simulation that was developed by security experts at Microsoft’s Threat Intelligence Center (MSTIC), a team that focuses on tracking the most sophisticated cyber actors in the world. The best part about this data is that it is fictitious and generated by a python script, meaning participants get to learn real techniques without the dangers of dealing with private data. This training gives participants the opportunity to learn and apply cyber threat analysis skills as they defend a simulated company from hackers.
